Concerned about user privacy? Well, you should if you want to avoid fines of up to €20 million. GDPR compliance is a must for pretty much every software company that handles EU residents’ data. To make the task easier, we created an in-depth guide to GDPR compliance for SaaS platform owners and software developers.
Feel free to read the whole article or jump straight to the GDPR implementation steps.
What is GDPR?
The General Data Protection Regulation (GDPR) aims to protect the privacy of EU residents. The regulation applies to companies that handle personal information of even one customer residing in Europe. Companies violating the regulation risk fines of up to €20M or 4% of annual global turnover, whichever is higher.
To further understand GDPR requirements, we should define the data subject, data controller, and data processor:
Meet Lucy. She is crazy about shopping. Lucy likes shopping on Amazon. To register on the website and buy things, Lucy gave out her personal data, including credit card and bank details. In this case, the girl is a data subject because the data is about her.
Amazon is a data controller because it decides how the data will be processed.
Amazon outsources its customer support to a third party call center. Employees in that call center have access to some records but can only use this data for very specific purposes. In this case, the call center is known as a data processor, as it deals and handles personal information in a limited way.
Here are some of the most important GDPR requirements for software compliance.
1. EU Residents have the right to know what you are doing with their data
GDPR clearly lays out what information data controllers and data processors (you) are obliged to provide upon a customer’s request:
- Who are you?
- Why do you have their data?
- Where did you get it from?
- How long will you have it?
- How and where is it processed?
2. Silence and inactivity are no longer signs of consent for processing personal data
Under the GDPR, consent has to be freely given and specific to each processing activity. It must be a statement of clear permissive action.
3. You should handle customer’s sensitive personal information more carefully
Under GDPR, this information is extra sensitive and can not be freely used, shared, and processed without explicit consent from the data subject:
- Religious or philosophical beliefs.
- Physical and mental health.
- Data concerning sex life.
- Racial or ethnic origin.
- Trade-union membership.
- Political opinions.
- Biometric and genetic data.
3. The time for data breach notification is 72 hours
You must notify users of any type of data breach, within 72 hours. Inform data subjects directly if the result of the breach might cause them significant harm (e.g. disclosure of their bank account details or sensitive data relating to their children).
4. Right to be Forgotten — a user should be able to disappear from all your backups
At any stage, the user may request to delete their information. You must delete any records with personal data and never use them again. This includes database records, backup copies, files, and any copies that may have been moved into an archive.
According to the law, you have less than one month to do so.
5. A user has the right to transmit the data to another processing system
In other words, a data subject has the right to transfer their data to your competitor. This right puts more power in the hands of individuals to swap to any other data controller/processor.
Are you liable to GDPR?
As a custom software development company, we often get this question from our American customers. We recommend such customers to answer four questions:
- Do EU citizens use your solution?
- Is there a subscription function in your software?
- Do you have any comments sections?
- Can users log in to your website with third-party apps?
Answering “yes” at least to one question means that you’re liable to GDPR. This means that pretty much all SaaS founders need to understand how to be GDPR-compliant.
Now, let’s go from GDPR requirements to some practical steps.
GDPR implementation: 15 steps to SaaS data protection
These are the key steps of GDPR compliance for SaaS platform owners.
1. Consider whether you really need all the data you collect
When making GDPR-compliant software, check what kind of personal data it stores. Do you really need this data? The best course for the privacy-conscious future is to collect only the bare minimum of personal data.
2. Encrypt all personal data
Encryption scrambles data in a way that makes it unintelligible for those who don’t have the decryption keys. The word “encryption”is only mentioned 4 times throughout the GDPR text:
- “…implement measures to mitigate those risks, such as encryption.” (P51. (83))
- “…appropriate safeguards, which may include encryption” (P121 (4.e))
- “…including inter alia as appropriate: (a) the pseudonymisation and encryption of personal data.” (P160 (1a))
- “…unintelligible to any person who is not authorized to access it, such as encryption” (P163 (3a))
However, data breaches are inevitable. In July 2015, hackers attacked Ashley Madison and stole more than 25 GB of personal data from the adultery dating website. The information, including names, emails, and addresses, was stored as plain text. This allowed anyone to track the would-be cheaters. This negligence resulted in a wave of blackmail, ruined careers, and broken marriages.
Website owners had to pay over $11 million to settle ensuing lawsuits. Moreover, at least three people have committed suicide due to Ashley Madison breach.
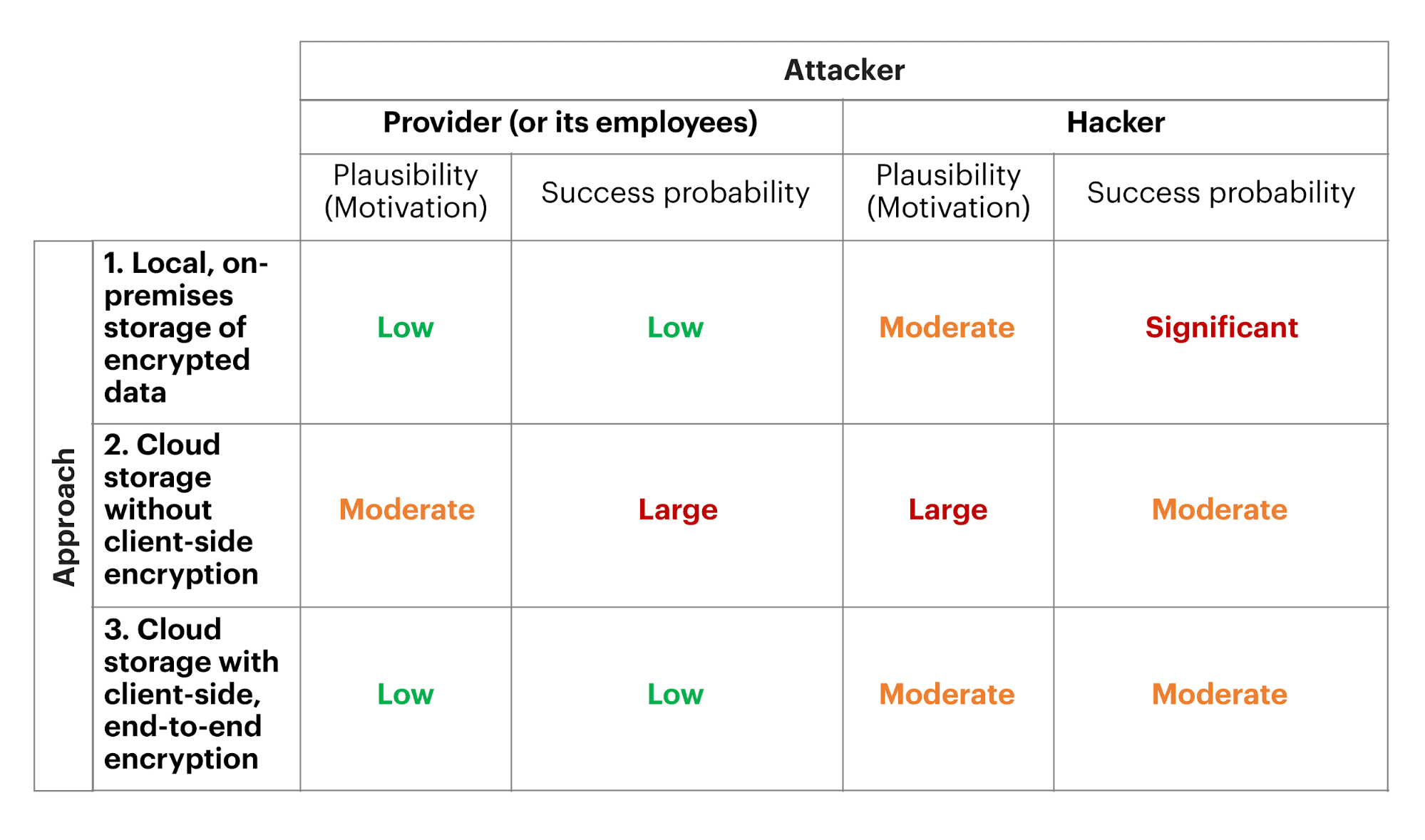
End-to-end encryption is your best bet at mitigating the damage of a possible data breach.
Source: tresorit.com
But what if for some legitimate reason, such as cost-efficiency or drop in performance, you can’t use encryption as a part of your data protection policy?
In such a case, you should either gather enough evidence to back up your claims or use alternative methods such as pseudonymization.
3. Consider HTTPS an essential part of your application
“Contact us” forms often contain personal data such as emails, phones, or home addresses. If you store and send this information as plain text, you’re opening the door to hackers.
So again, use encryption for the “contact us” forms. Also, inform your clients how you store this data and for how long.
The next step is to employ HTTPS, a secure version of the HTTP communication protocol.
It encrypts all the data sent between a client and a server using the SSL/TLS cryptographic protocols. When a user requests an HTTPS connection to your application, it sends him/her your SSL certificate that contains the key required to initiate the secure connection.
That’s why it’s important to receive an SSL certificate from a credible Certificate Authority and correctly install it. Also, make sure that your certificate isn’t susceptible to the protocol vulnerabilities.
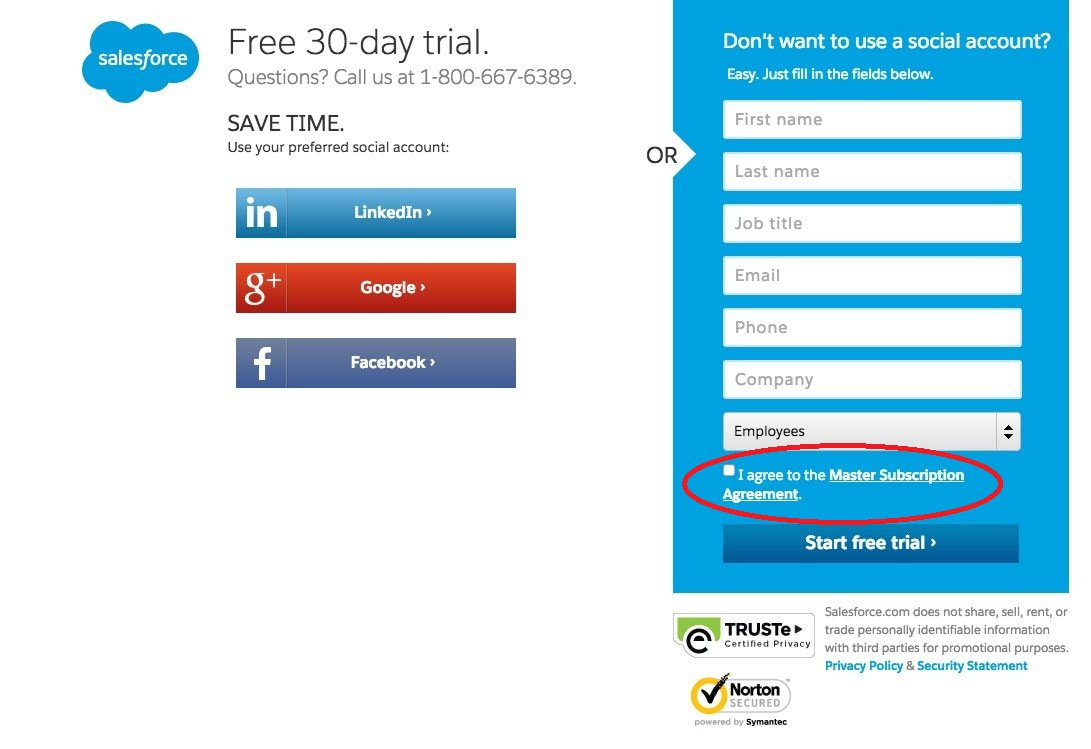
4. Get your consent forms in order
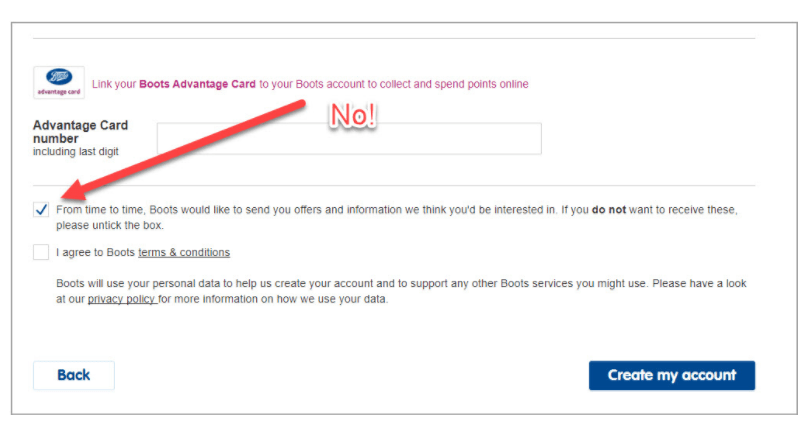
Forget about any kind of pre-ticked boxes. You can no longer get away with implicit, opt-out consent. GDPR requires “a statement of clear affirmative action” or “ a freely given, specific, informed, and unambiguous user consent”.
Consent forms must default to a “no” or be blank. In such a way you don’t force users to actively opt-out.
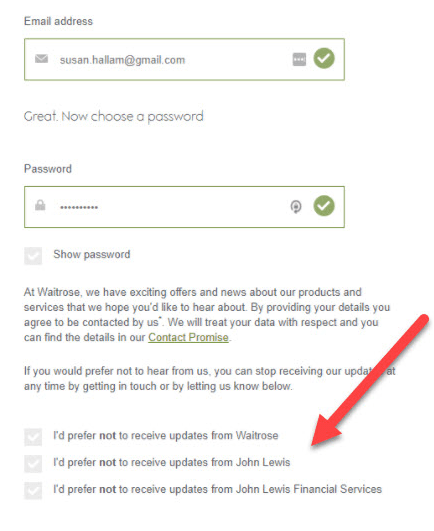
5. Implement granular opt-in
As a platform owner, you want to occasionally reach out to clients for marketing purposes. You need to ask explicit consent for each type of data processing you handle.
This means that if you’d like to sent promo materials via email, phone, and post, your consent form should have three separate opt-in boxes:
If all you need for your marketing is the email address, a marketing consent will suffice.
For personalization, segmentation, or targeting, you’ll need both marketing consent and consent (or legitimate interest) to collect and profile any additional behavioral or demographic data.
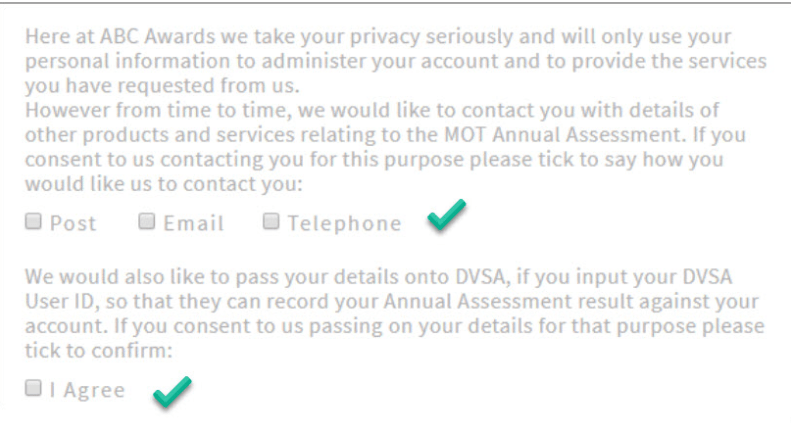
6. Be specific about the third parties
If you pass personal data to third parties, accurately identify and name each of these parties in your consent forms.
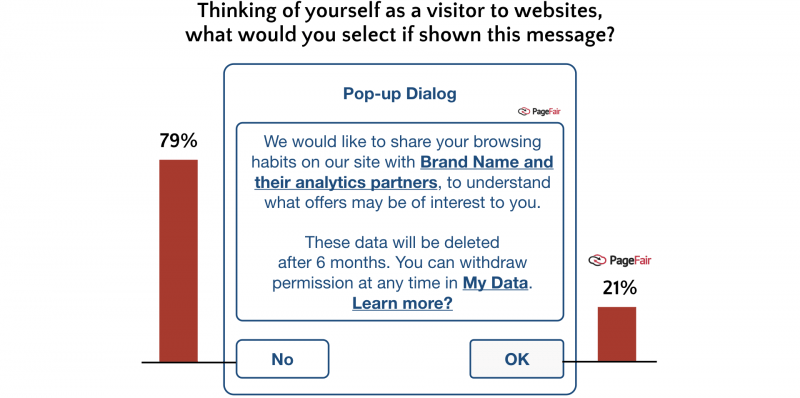
Note how each permission in the picture above has its own checkbox. The mistake in this example is having to opt-out of the permission instead of opt-in. This is a big NO under GDPR.
Still, giving third parties access to the personal data of your users for analytics or other purposes is definitely a bad idea.
Source: PageFair.com
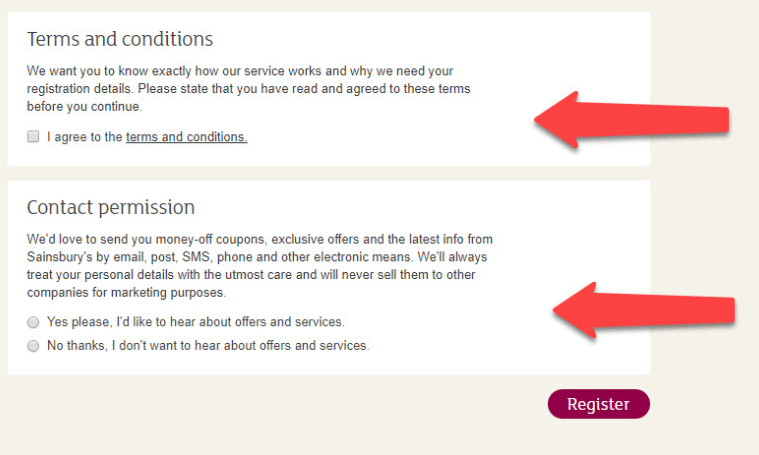
7. Separate the Terms and Conditions agreement from other consent forms
Request Terms and Conditions agreement separately for any kind of personal data handling.
8. Make Terms and Conditions section highly visible
Under GDPR, you’re no longer allowed to hide your Terms and Conditions or bury it in the fine print. The following scheme is no longer appropriate:
Users have to acknowledge they’ve read the Terms and Conditions and agree to them before getting access to your app.
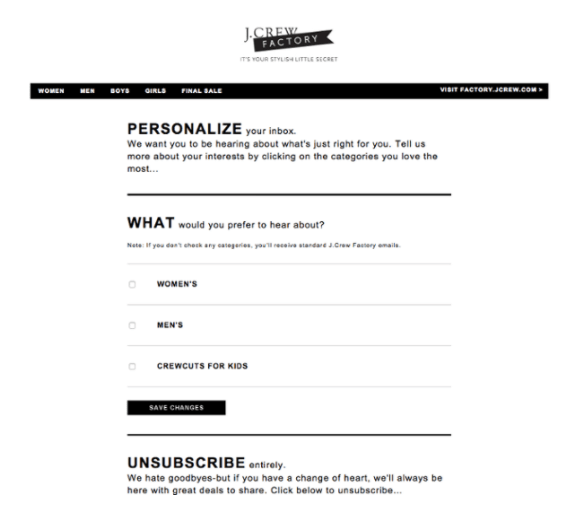
9. Make sure users can easily withdraw their consent
Due to the new GDPR principle – the Right to be Forgotten – a user must be able to unsubscribe and remove their consent at any time. For example, if you send newsletters, your emails should contain the “unsubscribe” feature.
10. Change your cookie policies
The official GDPR document mentions cookies in the following context (Recital 30):
Natural persons may be associated with online identifiers […] such as internet protocol addresses, cookie identifiers or other identifiers […]. This may leave traces which, in particular when combined with unique identifiers and other information received by the servers, may be used to create profiles of the natural persons and identify them.
In simpler words, the cookies that allow you to identify users via their devices (advertising, analytics, and functional cookies) are subject to GDPR. In 2024, you should either avoid using such cookies or find lawful ground for collecting and processing personal data:
- Legal obligations.
- Legitimate interests (as long as they don’t violate individual rights).
- Requirements for a contract execution (i.e. gathering payment data from contractors).
- Explicit user consent.
Under GDPR, the act of visiting your website for the first time doesn’t automatically grant consent for processing personal data. Displaying messages like “If you use this website, you accept cookies” isn’t considered a “freely given consent” (Recital 42).
Granular consent still applies. So, if you want to track visitor behavior and use their data for advertising, obtain consent for each activity.
According to the GDPR best practices, you must allow visitors to easily withdraw their consent. Remember, you can’t block access for users who withhold consent. And after they log out, you’ll have to destroy their cookies and sessions.
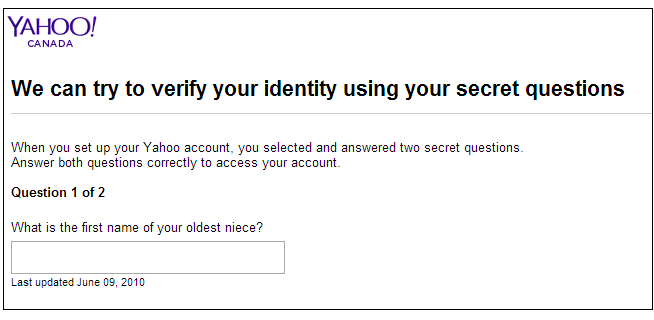
11. Avoid security questions that disclose personal information
Users who sign up for SaaS applications often get security questions:
This is a big NO for GDPR software compliance. In 2024, security questions mustn’t contain any information related to the customer’s family, preferences, homes, etc.
The best option is to use two-factor authentication (2FA). It combines a password with another identifier such as a phone number, fingerprints, and so on. Such systems are a powerful deterrent for cybercriminals.
If this option isn’t possible, let users create their own secret questions. Just warn them against disclosing personal information.
12. Inform users about logs containing their IP addresses
Check if your system uses IP addresses or location data in authentication. If your logs contain such data, inform users about the way you store them and how long they persist in your system. Encrypt the logs and ensure they contain no data that’s particularly sensitive, like passwords.
13. Remove all personal data after being passed to payment gateways
Using payment gateways often means collecting personal data.
In most cases, this data remains in your system, which is illegal under the GDPR. Your application must delete any personal data within a set period (e.g. 60 days).
14. Allow users to reject your business intelligence tracking
SaaS applications often track visitor behavior and tastes to improve recommendations. Under GDPR, such activities require a clear and explicit consent. You’ll also have to tell users how this data is stored in your systems and for how long.
If a user rejects tracking, respect their choice!
15. Erase unsubscribed user data
According to GDPR’s Right to be Forgotten, users are free to delete their accounts together with all their personal data. Your task is to clearly show them that this data will indeed be deleted as well as erased from all your backups.
Treating the deleted accounts as merely inactive will be viewed as an infringement of the law.
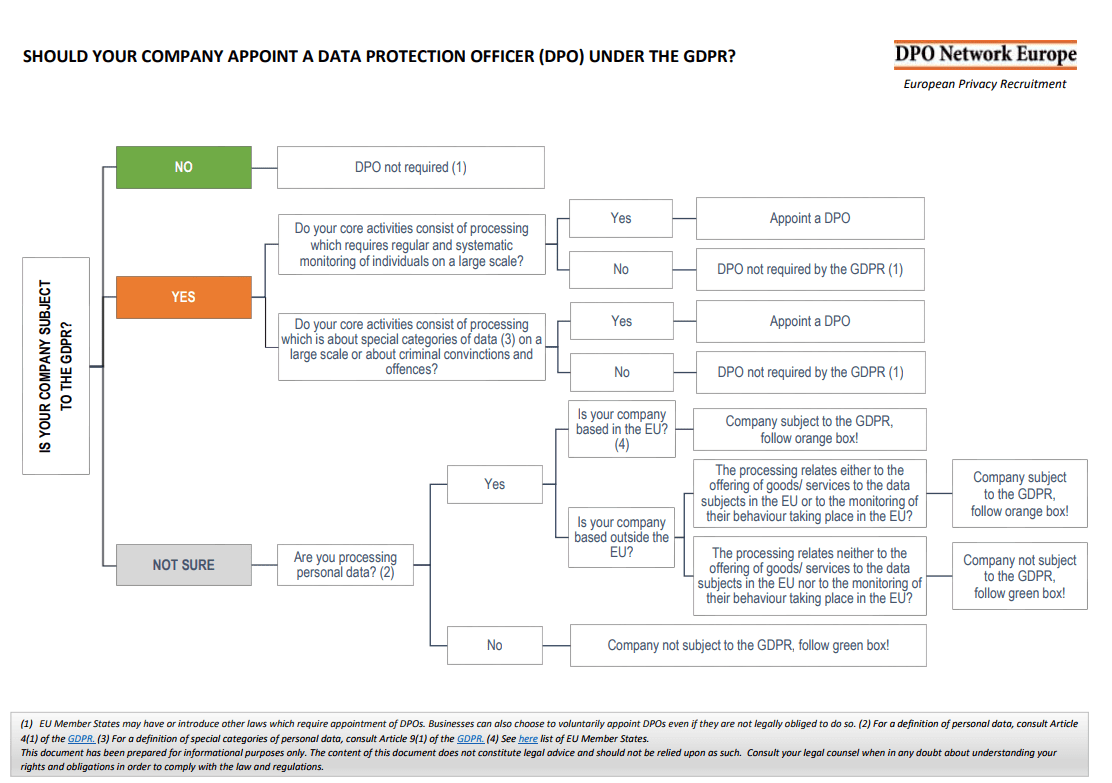
Bonus: do you need a data protection officer (DPO)?
Do your core activities include handling personal and sensitive data or systematically monitoring customer behavior on a large scale? Those who answered “yes” do, in fact, need to appoint a data protection officer. According to articles 37-39 of EU GDPR, such a person should possess expert knowledge of the data protection law and practices to:
- Make all the employees of your company aware of their obligations under GDPR.
- Control strict compliance with GDPR.
- Report to higher authorities about personal data processing states.
- Consider and evaluate all the possible risks associated with data protection processes under GDPR.
Conclusion
Now you know how to make your software GDPR-compliant. Following these steps will make it easy for you to improve SaaS data protection. In privacy-conscious times, the ability to ensure security and transparency will remain a huge advantage.
And if you need assistance, you can always rely on MindK to take care of GDPR implementation. We’re a product development studio with a focus on human-centered design, AI, and cloud technologies.
Just drop us a line to schedule a free, no-obligations consultation with our experts.