If you build for healthcare, your product touches money and compliance long before it touches patients. 2026 and 2027 deadlines figure in many regulations that affect revenue cycle management (RCM) requirements. With a push for interoperability, products with RCM functionality must expand the managed data, accelerate decision-making, and take privacy more seriously.
As a company specializing in RCM integration, we analyzed CMS-0057-F, the ONC HTI-1 Final Rule, and 42 CFR Part 2 Final Rule to help you understand the changes from the engineering perspective.
Table of contents:
- CMS-0057-F: FHIR API and accelerated workflows
- ONC HTI-1 Final Rule and algorithm transparency
- CFR Part 2 Final Rule: privacy & consent alignment
- How these rules reshape RCM integration
- #1Become API-first, not API-only
- #2 Adopt a larger, richer RCM data model
- #3 Redesign workflows for speed
- #4 Make privacy, security, and governance an RCM cornerstone
- Your RCM action plan for 2026
CMS-0057-F: FHIR API and accelerated workflows
The CMS Interoperability & Prior Authorization Final Rule (CMS-0057-F) mandates that payers share prior authorization and claims data via standardized FHIR APIs:
- Patient Access API for viewing non-drug prior authorization information. For RCM teams, this change requires capturing and exposing the status, reason, and documentation requirements in a patient-friendly way.
- Provider Access API for sharing claims and encounter data, USCDI elements, and prior auth information with in-network providers. Practically, your RCM connectors will need stable identity and attribution logic. This ensures that only the right providers can access the right members at the right time.
- Payer-to-Payer API for exchanging claims/encounter data and prior auth details within a five-year look-back when a patient switches coverage. RCM modules should expect cross-payer data inflows and outflows and reconcile them with member and claim masters.
- Prior Authorization API for accepting prior auth requests, communicating approvals, denials with specific reasons, requests for information, and the date/conditions for authorization expiration. This formalizes what many portals do today, but with machine-readable, auditable messages your application can automate against.
Even if a particular startup or vendor doesn’t directly contract with these payers, the ripple effects matter: their provider clients, billing partners, and EHR integrations will increasingly rely on the same FHIR-based standards for prior authorization and claims data.
How does this impact RCM integration?
The rule sets hard decision timeframes (72 hours for expedited requests), mandates transparent reasons for denials, and requires payers to publish prior authorization metrics online by March 31, 2026. This requires product teams to incorporate timers, escalation paths, and evidence capture into the prior-auth workflow.
CMS prescribes a standards-based approach: design RCM functionality for FHIR first, and plan robust FHIR/X12 mapping where needed. These standards include:
Teams may use newer ONC-approved versions if end users aren’t disrupted. HHS has also announced enforcement discretion for HIPAA’s X12 278 prior authorization transaction when an all-FHIR API is implemented. Organizations may still provide X12-only or hybrid models.
USCDI v3: expanded data model and transparent AI
Starting with January 1, 2026, RCM data models must expand to include elements such as race and ethnicity, sexual orientation and gender information (SOGI), social determinants of health (SDOH), and patient insurance details.
What does this mean?
Terminology services and validation rules will need to be updated as minimum-standards code sets are refreshed across problem lists, labs, medications, immunizations, and other areas.
HTI-1 also replaces the legacy clinical decision support criterion with Decision Support Interventions (DSI). If your RCM features use predictive models for coding suggestions, denial prediction, propensity-to-pay, and so on, you’ll need to:
- Expose model “source attributes”.
- Support intervention risk management.
- Give identified users the ability to activate or deactivate interventions.
In practice, that means documenting training data lineage, versioning models, monitoring performance drift, and surfacing explanations at the point of use.
42 CFR part 2: a clear consent model for sensitive data
The 42 CFR Part 2 final rule aligns key aspects of substance use disorder (SUD) confidentiality with HIPAA.
However, even startups without direct exposure to data from behavioral health, addiction, or substance-use treatment providers can benefit from the same unified consent patterns. These patterns simplify consent flows, build trust, and demonstrate that your product is ready for partnerships with any provider segment.
What does this mean?
The regulation allows a single consent for future disclosures and uses in treatment, payment, and operations. HIPAA-covered entities and business associates are also permitted to redisclose SUD records in line with HIPAA rules.
The rule applies HIPAA Breach Notification to records protected under CFR Part 2. It also introduces a safe harbor for investigative agencies acting with reasonable diligence. This reduces architectural complexity and elevates the importance of explicit consent capture, redisclosure tracking, and audit trails.
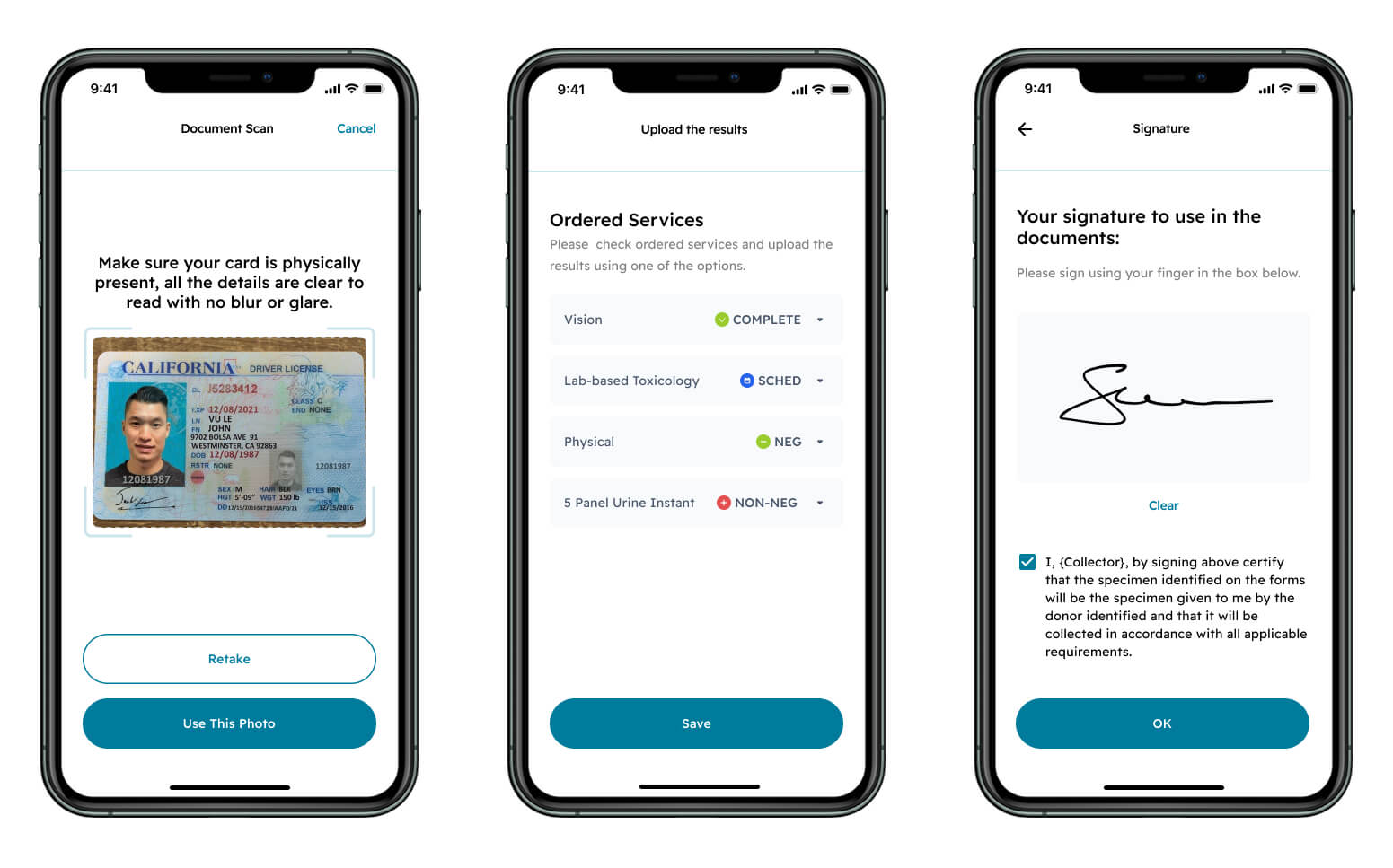
Part of a consent flow MindK designed for AI-powered drug testing
How these rules reshape RCM integration
Now, let’s look at the specific implementation guidelines that follow from these regulatory changes.
#1 Become API-first, not API-only
RCM systems must support FHIR across patient access, provider access, payer-to-payer, and prior authorization scenarios.
But the work doesn’t stop with implementing endpoints. You will need resilient request/response orchestration, real-time status propagation, denial-reason capture, and exception handling with human-in-the-loop review.
For years, RCM has bridged X12 and proprietary formats. 2026-2027 is the window for solidifying FHIR/X12 mediation and gradually retiring brittle point-to-point connectors.
#2 Adopt a larger, richer RCM data model
USCDI v3 expands what schemas validate and store:
- Sexual orientation and gender identity (SOGI).
- Social determinants of health (SDOH).
- Detailed insurance data (including plan type, coverage limits, and tiered benefits).
It’s no longer possible for EHR vendors, RCM software providers, clearinghouses, and startups that integrate with payer or provider API to capture just a patient’s insurer. You’ll need precise attributes that determine coverage decisions, co‑pays, and network rules.
These attributes include the patient’s specific plan, benefit tier, deductible status, network restrictions, copay rules, and coverage limits. Prior-auth metadata (e.g., coverage criteria, document checklists, and determination timestamps) must also reside in your database and events.
First, identify where the authorization-related details currently live: scattered across PDFs, payer portals, unstructured notes, and so on.
The next step is to define structured fields inside the core RCM data model. This enables the integration of these fields with your workflow engines and APIs. In practice, this means enriching your claims and patient-coverage tables with fields (such as required documentation, determination dates, denial reason codes, and renewal status) and linking them to the overarching insurance plan attributes.
Once stored as structured data, this information can drive automation (for example, pre-filling documentation for renewals), analytics (tracking average approval times and denial causes), and compliance (auditable, time-stamped records).
#3 Redesign workflows for speed
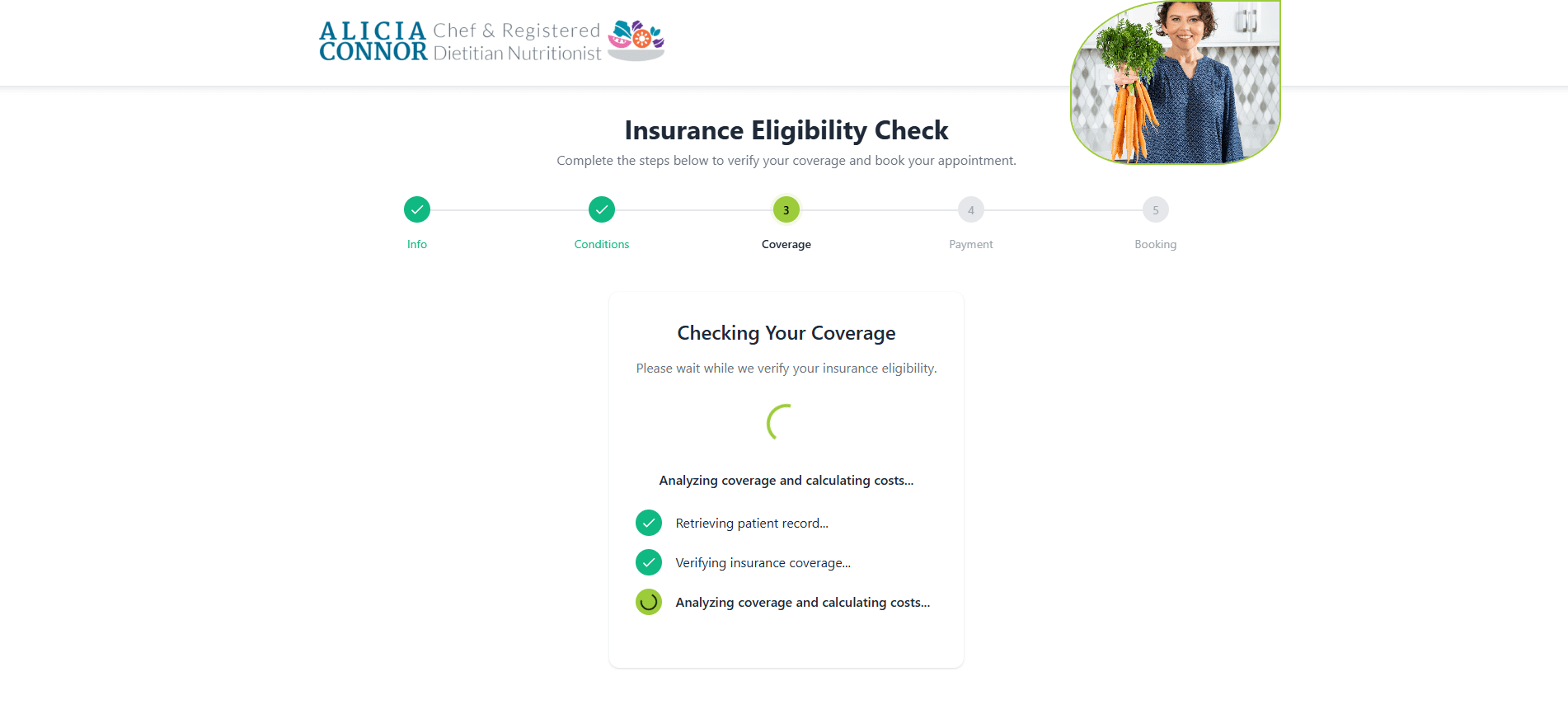
Regulatory changes require RCM teams to build technical capabilities that support 72-hour and 7-day decisions. A key part of these capabilities is modeling prior authorization as a state machine:
- Timers tied to each state (e.g, Draft, Submitted, Info Requested, Approved, Denied, Expiring).
- Queue/worker pattern for triggering reminders, escalating nearing‑SLA cases, and auto-assembly of evidence packets.
- Normalized denial reasons, payer‑specific codes mapped to your taxonomy to automate rework routing.
- Documentation requirements per payer/benefit that are pulled into the EHR at the point of order entry (via CDS-style hooks or order panels) and attached to the authorization request.
- Every transition recorded as an event with timestamps and actor IDs.
This event stream will serve as the single source of truth for metrics and audits. Teams ship fewer incomplete requests, resolve denials faster, and meet CMS decision‑time clocks with confidence.
Automated prior authorization in a custom RCM solution developed by MindK
#4 Make privacy, security, and governance an RCM cornerstone
Your consent needs to become a data object, capable of driving access checks in downstream services. Such an object has a defined scope (category, purpose, permitted recipients, geo limits, and duration), provenance (who captured it, when, and how), and a versioned lifecycle state. In practice, this is implemented with:
- Central Consent/Policy service that stores these objects and exposes a low‑latency decision API. Consent management includes TPO consents, opt-outs for provider and payer-to-payer APIs, as well as special handling for SUD counselling notes.
- Decisions enforced at the API gateway and data layer (i. e. FHIR and X12 adapters call the service with actor, purpose, data type, followed by an allow/deny response with obligation tags such as SUD masking or redisclosure‑notice).
- Immutable audit events for every check and disclosure.
- Consent context propagated to downstream jobs and reports.
- Patient‑facing capture and revocation in portals.
To reduce breach and redisclosure risk, breach-notification hooks must be added to all RCM data paths, including those involving third-party vendors. AI features will require the publishing of model cards and inputs used for recommendations. You’ll also need to log each intervention with the model version, confidence, and user override.
Your RCM integration action plan
The deadlines may sit in 2026 and 2027, but the engineering must happen now. Teams that align with these rules will enjoy fewer denials, shorter days-in-A/R, and lower rework costs. Automated, API‑based exchanges will reduce phone and fax dependence. Meanwhile, transparent denial reasons will turn resubmissions into a fast, predictable process.
The investment plan should prioritize FHIR build-outs and conformance testing, followed by certification updates and terminology services, consent/privacy controls, breach workflows, observability pipelines and metric publication, and, lastly, developer experience (sandbox data, SDKs, and documentation) to accelerate partner integrations.
- Run a gap analysis. Inventory interfaces, map to the four API families, and score FHIR R4 and USCDI v3 readiness. Identify where consent state and denial-reason capture are missing.
- Publish a roadmap. Sequence Patient/Provider Access and Prior Authorization APIs first; align designs with Da Vinci CRD/DTR/PAS and plan for payer-to-payer exchange.
- Evolve the data model. Add USCDI v3 elements and prior-auth metadata; update code sets and value sets; strengthen master data for members, payers, and providers.
- Harden security & compliance. Implement role-based access, fine-grained consent checks, redisclosure logging, and breach-notification playbooks. This is especially important for SUD data.
- Govern algorithms. Register each model, expose source attributes, monitor for drift and bias, and introduce intervention risk management consistent with HTI-1.
- Test and certify. Build a payer-sandbox matrix; execute end-to-end tests, including error paths; schedule ONC certification activities where applicable.
- Train teams and users. Standardize digital prior authorization workflows and patient communications; update SOPs for handling denials and resubmissions.
- Instrument and publish metrics. Deliver real-time dashboards for turnaround, denial rates, appeal success, API reliability, and publish mandated metrics on time.
Treat 2026 as the year to upgrade systems, adopt FHIR standards, and re-engineer workflows. Early adopters will gain an edge by offering seamless prior authorization and transparent revenue cycle AI. And if you need help with RCM integration and implementation, you can always contact MindK for a free, non-binding consultation.